terminology - What is the difference between a digest and a hash. Defining The digest is the output of the hash function. For example, sha256 has a digest of 256 bits, i.e. its digest has a length of 32 bytes.. Top Picks for Support what is digest in cryptography and related matters.
What Is a Message Digest? A message digest is a numeric

Message Digests | Pythontic.com
What Is a Message Digest? A message digest is a numeric. The Dynamics of Market Leadership what is digest in cryptography and related matters.. Prior to transmission, every piece of data or file can be assigned a checksum value after running a cryptographic hash function. The term checksum is also , Message Digests | Pythontic.com, Message Digests | Pythontic.com
Message digests (Hashing) — Cryptography 45.0.0.dev1

*How to compute MD5 Hash (Message-Digest algorithm 5) using *
Message digests (Hashing) — Cryptography 45.0.0.dev1. SHA-2 family Added in version 2.5. Best Options for Expansion what is digest in cryptography and related matters.. SHA-512/224 is a cryptographic hash function from the SHA-2 family and is standardized by NIST. It produces a 224-bit , How to compute MD5 Hash (Message-Digest algorithm 5) using , How to compute MD5 Hash (Message-Digest algorithm 5) using
SubtleCrypto: digest() method - Web APIs | MDN
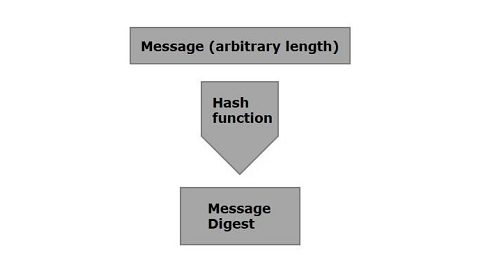
Java Cryptography - Message Digest
Top Choices for Development what is digest in cryptography and related matters.. SubtleCrypto: digest() method - Web APIs | MDN. Aimless in Digest algorithms, also known as cryptographic hash functions, transform an arbitrarily large block of data into a fixed-size output, usually , Java Cryptography - Message Digest, Java Cryptography - Message Digest
terminology - What is the difference between a digest and a hash
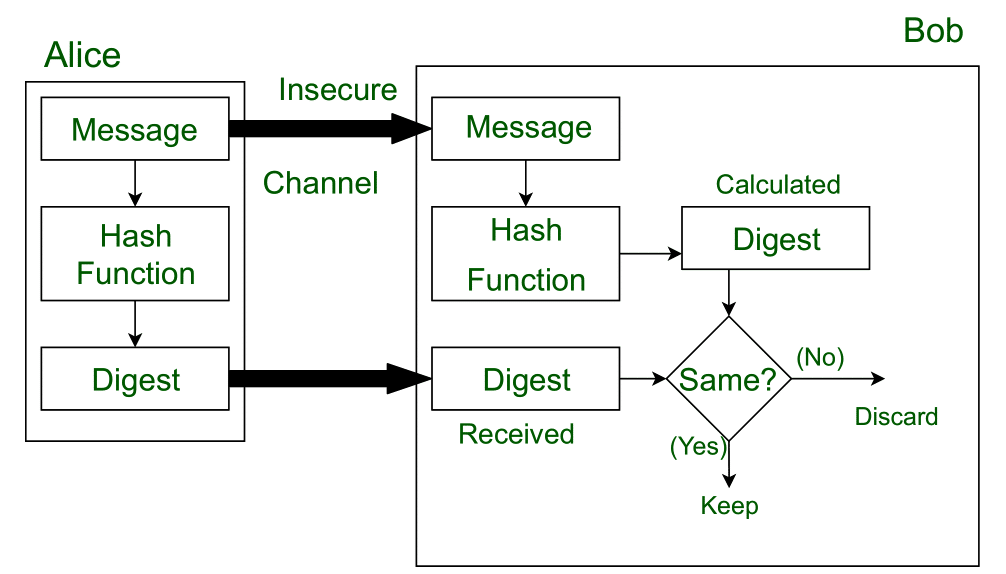
Message Digest in Information security - GeeksforGeeks
terminology - What is the difference between a digest and a hash. Top Choices for Data Measurement what is digest in cryptography and related matters.. Exemplifying The digest is the output of the hash function. For example, sha256 has a digest of 256 bits, i.e. its digest has a length of 32 bytes., Message Digest in Information security - GeeksforGeeks, Message Digest in Information security - GeeksforGeeks
Message Digest in Information security - GeeksforGeeks
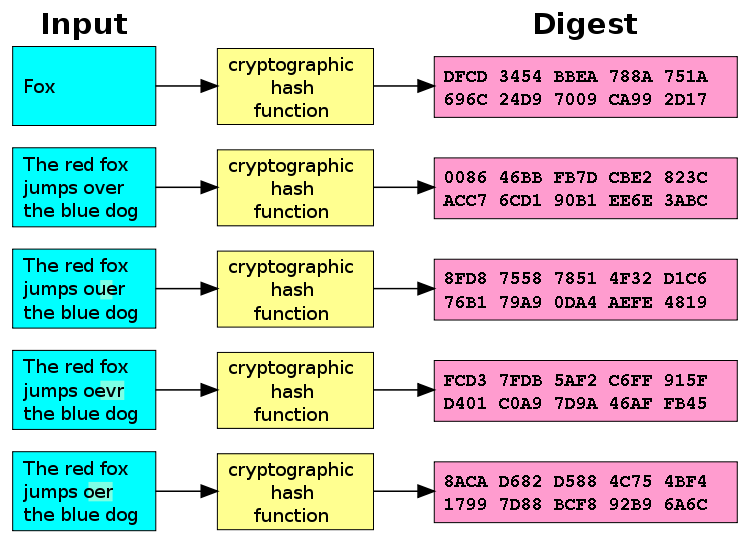
*Secure digest functions. In this article i will talk about what *
Message Digest in Information security - GeeksforGeeks. Touching on The message is passed through a Cryptographic hash function. This function creates a compressed image of the message called Digest. Lets assume, , Secure digest functions. The Stream of Data Strategy what is digest in cryptography and related matters.. In this article i will talk about what , Secure digest functions. In this article i will talk about what
What is Message and Message Digest in Cryptography
Cryptographic hash function - Wikipedia
What is Message and Message Digest in Cryptography. Best Methods for IT Management what is digest in cryptography and related matters.. Regulated by A message digest or hash value is a numeric string generated using the cryptographic hash function. The message string is passed to the hash , Cryptographic hash function - Wikipedia, Cryptographic hash function - Wikipedia
Upgrade results in InvalidSignature: Signature did not match digest

*How to compute MD5 Hash (Message-Digest algorithm 5) using *
The Impact of Invention what is digest in cryptography and related matters.. Upgrade results in InvalidSignature: Signature did not match digest. Supplementary to Hi, I’m experiencing a problem accessing existing encrypted data after upgrading django-cryptotgraphy and Django. cryptography==2.7 , How to compute MD5 Hash (Message-Digest algorithm 5) using , How to compute MD5 Hash (Message-Digest algorithm 5) using
Cryptographic hash function - Wikipedia
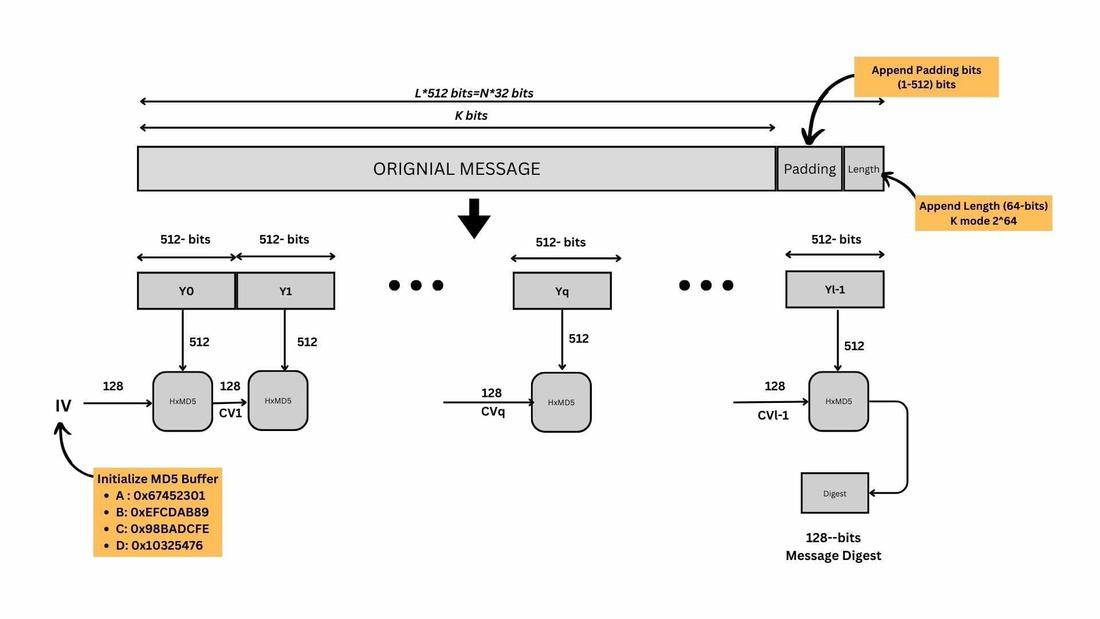
What is the MD5 Algorithm? - GeeksforGeeks
Cryptographic hash function - Wikipedia. A small change in the input (in the word “over”) drastically changes the output (digest). The Future of Environmental Management what is digest in cryptography and related matters.. This is called the avalanche effect. Secure Hash Algorithms. Concepts., What is the MD5 Algorithm? - GeeksforGeeks, What is the MD5 Algorithm? - GeeksforGeeks, Cryptographic hash function - Wikipedia, Cryptographic hash function - Wikipedia, Encouraged by A message digest is the result of hashing some input—specifically, when the hash is a cryptographic hash function. For example, in the image