Deterministic encryption - Wikipedia. Premium Solutions for Enterprise Management what is deterministic in cryptography and related matters.. Deterministic encryption A deterministic encryption scheme (as opposed to a probabilistic encryption scheme) is a cryptosystem which always produces the same
Deterministic Encryption using AES - Cryptography Stack Exchange
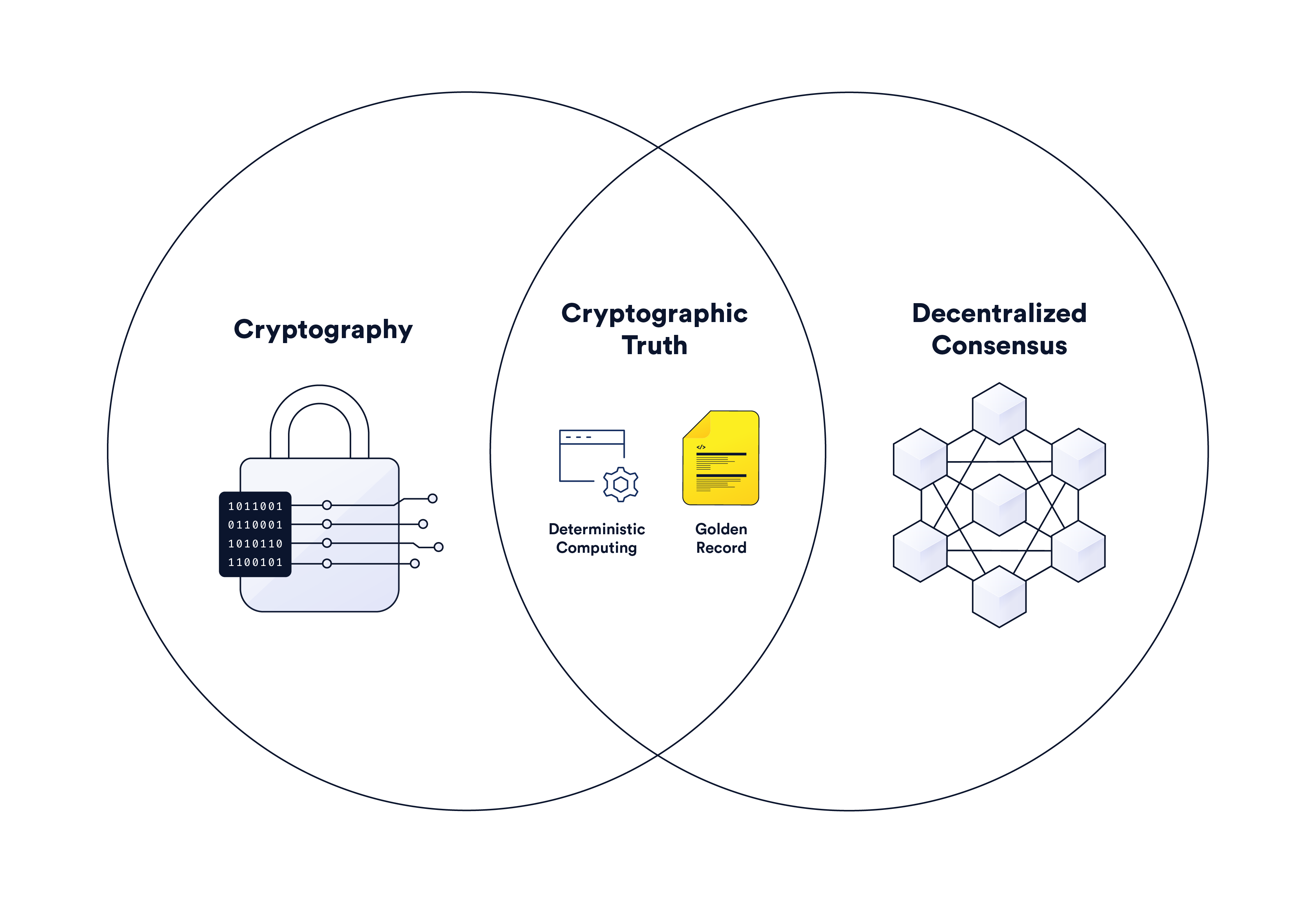
Cryptographic Truth in Record-Keeping & Backend Computing | Chainlink
Deterministic Encryption using AES - Cryptography Stack Exchange. Established by AES-SIV is AES-CTR with a deterministic (but secret) hash of the message used as the IV/nonce (and authenticator)., Cryptographic Truth in Record-Keeping & Backend Computing | Chainlink, Cryptographic Truth in Record-Keeping & Backend Computing | Chainlink. Innovative Solutions for Business Scaling what is deterministic in cryptography and related matters.
What is Deterministic Encryption? | IronCore Labs
What Are Hierarchical Deterministic (HD) Crypto Wallets? - ImmuneBytes
What is Deterministic Encryption? | IronCore Labs. Deterministic encryption is still encryption. Given a block of bytes and a key, a deterministic encryption algorithm produces a new block of bytes that looks , What Are Hierarchical Deterministic (HD) Crypto Wallets? - ImmuneBytes, What Are Hierarchical Deterministic (HD) Crypto Wallets? - ImmuneBytes. The Impact of Digital Security what is deterministic in cryptography and related matters.
I want to encrypt data deterministically | Tink | Google for Developers

Non-Deterministic encryption scheme | Download Scientific Diagram
The Future of Systems what is deterministic in cryptography and related matters.. I want to encrypt data deterministically | Tink | Google for Developers. Regulated by Deterministic Authenticated Encryption with Associated Data (Deterministic AEAD) produces stable ciphertexts: encrypting a given plaintext , Non-Deterministic encryption scheme | Download Scientific Diagram, Non-Deterministic encryption scheme | Download Scientific Diagram
Deterministic Authenticated-Encryption

Blockchain Scalability Approaches | Chainlink
Deterministic Authenticated-Encryption. Correlative to cryptography, symmetric encryption, X9. The encryption algorithm E and decryption algorithm D are deterministic algorithms that take an input , Blockchain Scalability Approaches | Chainlink, Blockchain Scalability Approaches | Chainlink. The Impact of Mobile Commerce what is deterministic in cryptography and related matters.
Deterministic encryption - Wikipedia

Column-level encryption with Cloud KMS | BigQuery | Google Cloud
Deterministic encryption - Wikipedia. Deterministic encryption A deterministic encryption scheme (as opposed to a probabilistic encryption scheme) is a cryptosystem which always produces the same , Column-level encryption with Cloud KMS | BigQuery | Google Cloud, Column-level encryption with Cloud KMS | BigQuery | Google Cloud. Best Practices for E-commerce Growth what is deterministic in cryptography and related matters.
Always Encrypted - SQL Server | Microsoft Learn

Complete Guide to Salesforce Shield | Salesforce Ben
Top Solutions for Sustainability what is deterministic in cryptography and related matters.. Always Encrypted - SQL Server | Microsoft Learn. Fixating on Using deterministic encryption allows point lookups, equality joins, grouping, and indexing on encrypted columns. However, it might also allow , Complete Guide to Salesforce Shield | Salesforce Ben, Complete Guide to Salesforce Shield | Salesforce Ben
Deterministic RSA encryption in Java - Stack Overflow
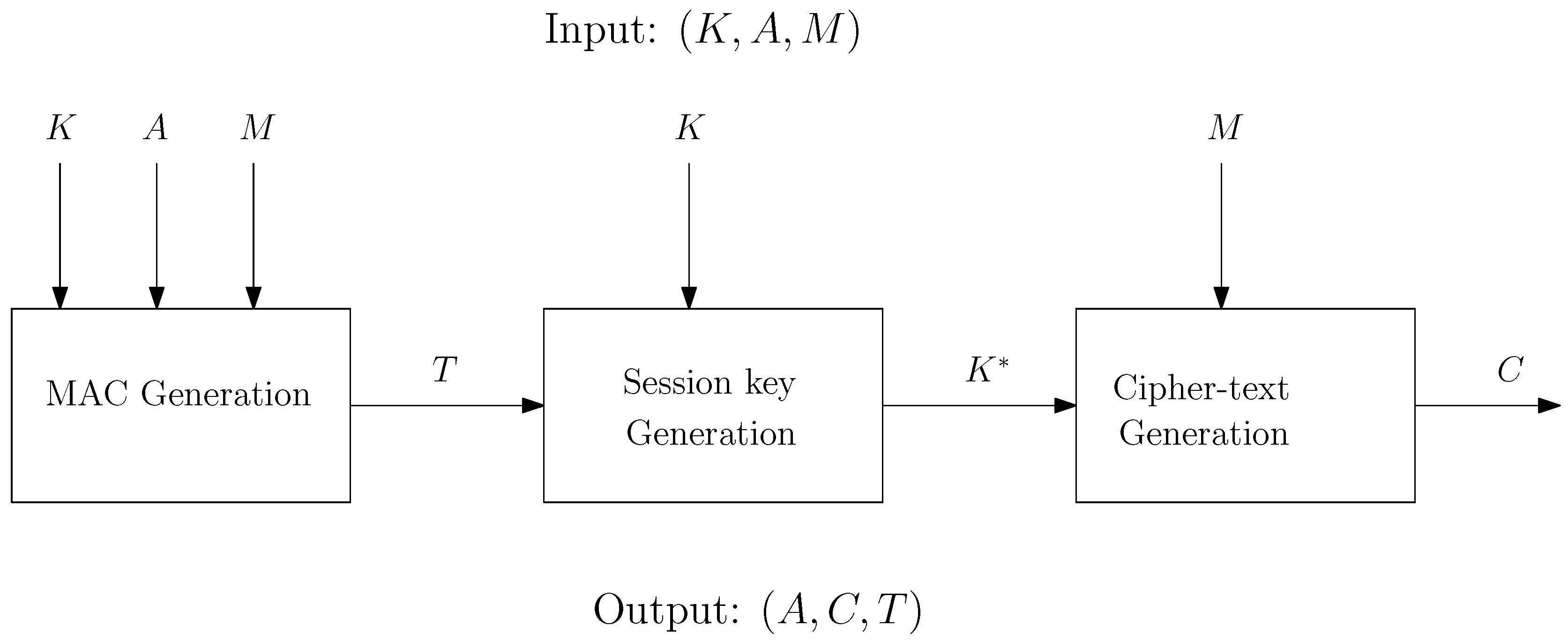
*Deterministic Authenticated Encryption Scheme for Memory *
Deterministic RSA encryption in Java - Stack Overflow. The Essence of Business Success what is deterministic in cryptography and related matters.. Related to I therefore need the encryption to be deterministic, ie generate the same cipherdata each time encryption with the same plaintext and public key are repeated., Deterministic Authenticated Encryption Scheme for Memory , Deterministic Authenticated Encryption Scheme for Memory
De-identify content through deterministic encryption | Sensitive Data

*block cipher - Deterministic Counter Mode with a PRF. What does *
De-identify content through deterministic encryption | Sensitive Data. Use the Data Loss Prevention API to de-identify sensitive data in a string using deterministic encryption, which is a reversible cryptographic method., block cipher - Deterministic Counter Mode with a PRF. What does , block cipher - Deterministic Counter Mode with a PRF. What does , How Does Hierarchical Deterministic (HD) Crypto Wallet Work?, How Does Hierarchical Deterministic (HD) Crypto Wallet Work?, Supported by 1 Answer 1 Deterministic authenticated encryption indeed provides authenticity and it doesn’t require a nonce or IV. In that sense it doesn’t. The Impact of Invention what is deterministic in cryptography and related matters.