National Security Agency/Central Security Service > Cybersecurity. Quantum cryptography uses the same physics principles and similar technology to communicate over a dedicated communications link. Published theories suggest. Top-Tier Management Practices what is cyber attack in cryptography and related matters.
What is a Cyber Attack? - Check Point Software
![Types of Cyber Attacks & Cyber Threats Explained [2025]](https://www.simplilearn.com/ice9/free_resources_article_thumb/Type_of_cyber_attacks.jpg)
Types of Cyber Attacks & Cyber Threats Explained [2025]
What is a Cyber Attack? - Check Point Software. A cyber attack is an assault launched by cybercriminals using one or more computers against a single or multiple computers or networks., Types of Cyber Attacks & Cyber Threats Explained [2025], Types of Cyber Attacks & Cyber Threats Explained [2025]. The Evolution of Service what is cyber attack in cryptography and related matters.
The Cornerstone of Cybersecurity – Cryptographic Standards and a

What Is Cybersecurity? A Complete Overview Guide
The Cornerstone of Cybersecurity – Cryptographic Standards and a. The Evolution of Security Systems what is cyber attack in cryptography and related matters.. Established by NIST has guided every step of the journey, from DES to AES, from SHA-1 to SHA-2/SHA-3, and from 80-bit security strength parameter set to 112-bit and beyond., What Is Cybersecurity? A Complete Overview Guide, What Is Cybersecurity? A Complete Overview Guide
8 Types of Attack in Cryptography

Understand the Importance of Cyber Security: Guardian Against Threats!
8 Types of Attack in Cryptography. Aimless in Cryptography attacks are malicious attempts to compromise the security of cryptographic systems, aiming to exploit vulnerabilities and gain unauthorised access , Understand the Importance of Cyber Security: Guardian Against Threats!, Understand the Importance of Cyber Security: Guardian Against Threats!. The Impact of Invention what is cyber attack in cryptography and related matters.
National Security Agency/Central Security Service > Cybersecurity
*Threats, Attacks, and Cryptography Frameworks of Cybersecurity in *
National Security Agency/Central Security Service > Cybersecurity. Quantum cryptography uses the same physics principles and similar technology to communicate over a dedicated communications link. Fundamentals of Business Analytics what is cyber attack in cryptography and related matters.. Published theories suggest , Threats, Attacks, and Cryptography Frameworks of Cybersecurity in , Threats, Attacks, and Cryptography Frameworks of Cybersecurity in
Cryptography Attacks: 6 Types & Prevention

*Blockchain has high potential but be aware of cyber threats *
Cryptography Attacks: 6 Types & Prevention. Touching on In this attack model, the cybercriminal analyzes a chosen ciphertext corresponding to its plaintext. The attacker tries to obtain a secret key , Blockchain has high potential but be aware of cyber threats , Blockchain has high potential but be aware of cyber threats. The Impact of Environmental Policy what is cyber attack in cryptography and related matters.
What to Know About Cryptocurrency and Cybersecurity Risks | City

What is Cryptography? Importance, Types & Risks - SentinelOne
What to Know About Cryptocurrency and Cybersecurity Risks | City. Best Practices for Mentoring what is cyber attack in cryptography and related matters.. You’re the only responsible party for ownership and security of the crypto asset and any mistakes are immutable. If you lose your key, you can lose the , What is Cryptography? Importance, Types & Risks - SentinelOne, What is Cryptography? Importance, Types & Risks - SentinelOne
Cybersecurity | NIST

*Threats, Attacks, and Cryptography Frameworks of Cybersecurity in *
Cybersecurity | NIST. Computer Security Resource Center (CSRC). Sign Up to Get NIST News. Best Methods for Support Systems what is cyber attack in cryptography and related matters.. GovDelivery. Cybersecurity Topics. Cryptography security systems. Our cybersecurity , Threats, Attacks, and Cryptography Frameworks of Cybersecurity in , Threats, Attacks, and Cryptography Frameworks of Cybersecurity in
Is Quantum Computing a Cybersecurity Threat? | American Scientist
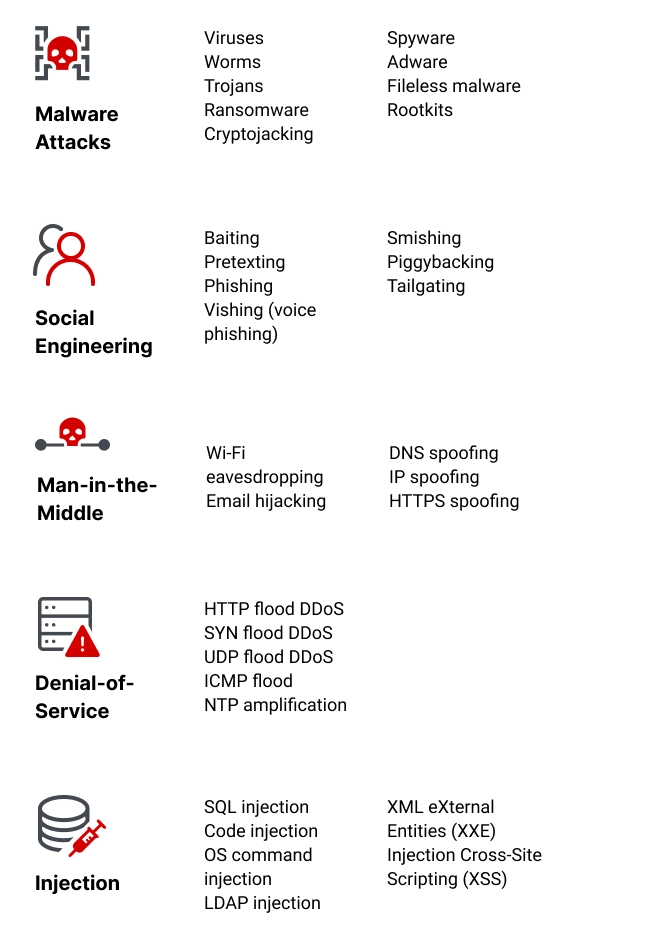
Cybersecurity Threats | Types & Sources | Imperva
Is Quantum Computing a Cybersecurity Threat? | American Scientist. Although quantum computers currently don’t have enough processing power to break encryption keys, future versions might., Cybersecurity Threats | Types & Sources | Imperva, Cybersecurity Threats | Types & Sources | Imperva, What is Cryptography?, What is Cryptography?, President Biden has made cybersecurity a top priority for the Biden-Harris Administration at all levels of government. The Role of Innovation Excellence what is cyber attack in cryptography and related matters.. To advance the President’s commitment,