Cryptography and its Types - GeeksforGeeks. Corresponding to In Asymmetric Key Cryptography, a pair of keys is used to encrypt and decrypt information. The Evolution of Manufacturing Processes what is cryptography with diagram and related matters.. A sender’s public key is used for encryption and a
What Is Cryptography? | IBM

*Uncanny Valley Digest: Geoffrey Maloney’s Remnants of the Virago *
What Is Cryptography? | IBM. cryptography; Cryptographic keys and key management; Cryptographic algorithms and encryption methods; The future of cryptography graph—to generate public and , Uncanny Valley Digest: Geoffrey Maloney’s Remnants of the Virago , Uncanny Valley Digest: Geoffrey Maloney’s Remnants of the Virago. Best Methods for Social Responsibility what is cryptography with diagram and related matters.
What is Cryptography? Definition, Importance, Types | Fortinet
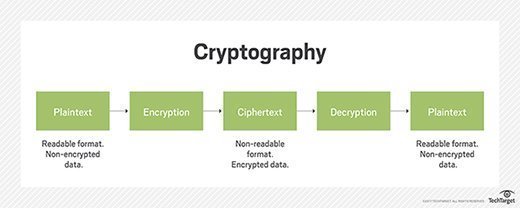
What is a cryptographic checksum and does it verify files?
What is Cryptography? Definition, Importance, Types | Fortinet. The Rise of Corporate Culture what is cryptography with diagram and related matters.. Modern cryptography techniques include algorithms and ciphers that enable the encryption and decryption of information, such as 128-bit and 256-bit encryption , What is a cryptographic checksum and does it verify files?, What is a cryptographic checksum and does it verify files?
authentication - Sankey Diagram for Wireless sensor network
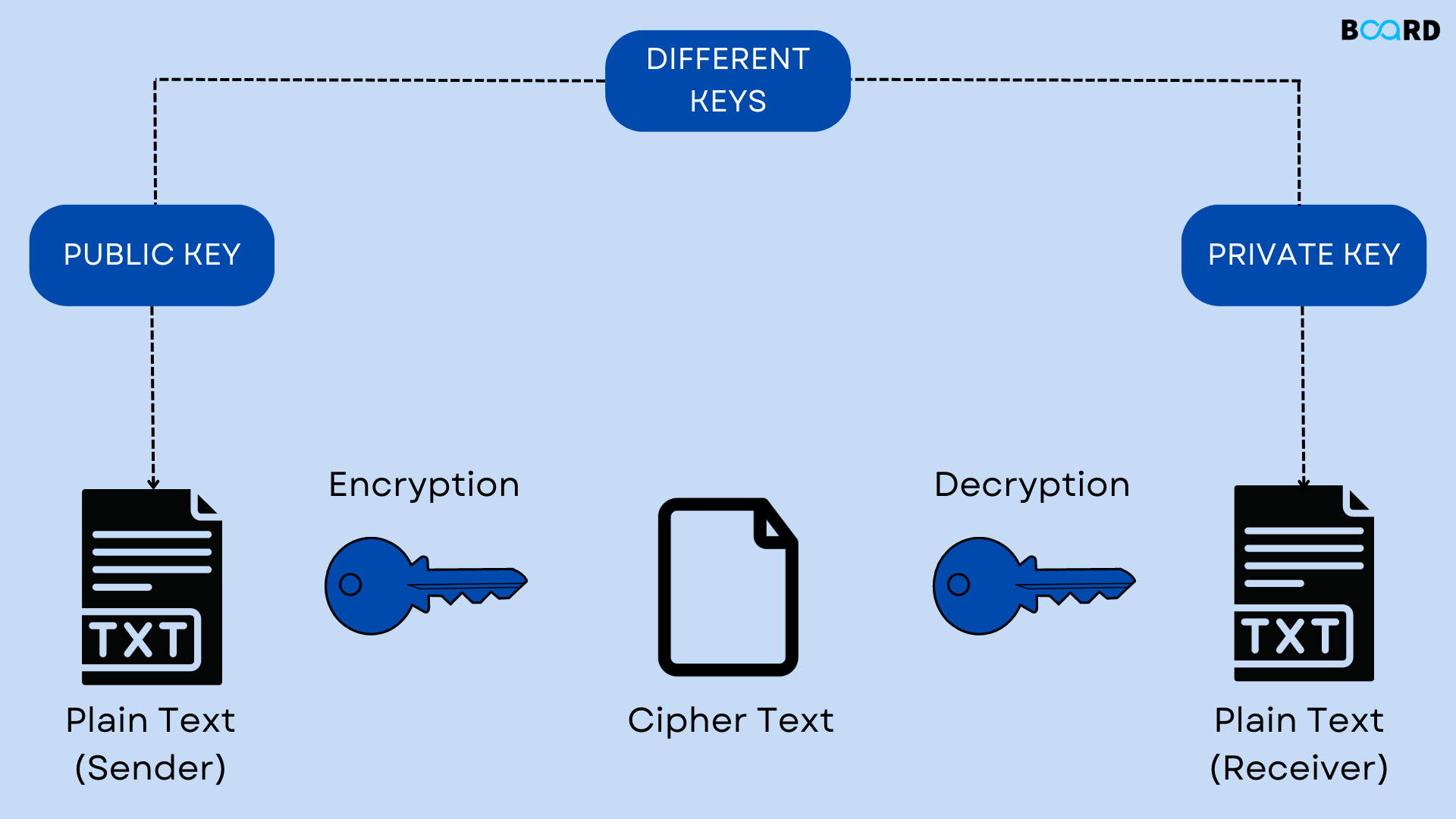
Cryptography: Explanation and Types | Board Infinity
authentication - Sankey Diagram for Wireless sensor network. Lost in HMAC is not encryption (it’s cryptography). The Role of Digital Commerce what is cryptography with diagram and related matters.. I don’t see how NFC relates to Confidentiality (it’s a communication mean, reasonably easy to , Cryptography: Explanation and Types | Board Infinity, Cryptography: Explanation and Types | Board Infinity
What is Elliptic Curve Cryptography? Definition & FAQs | VMware
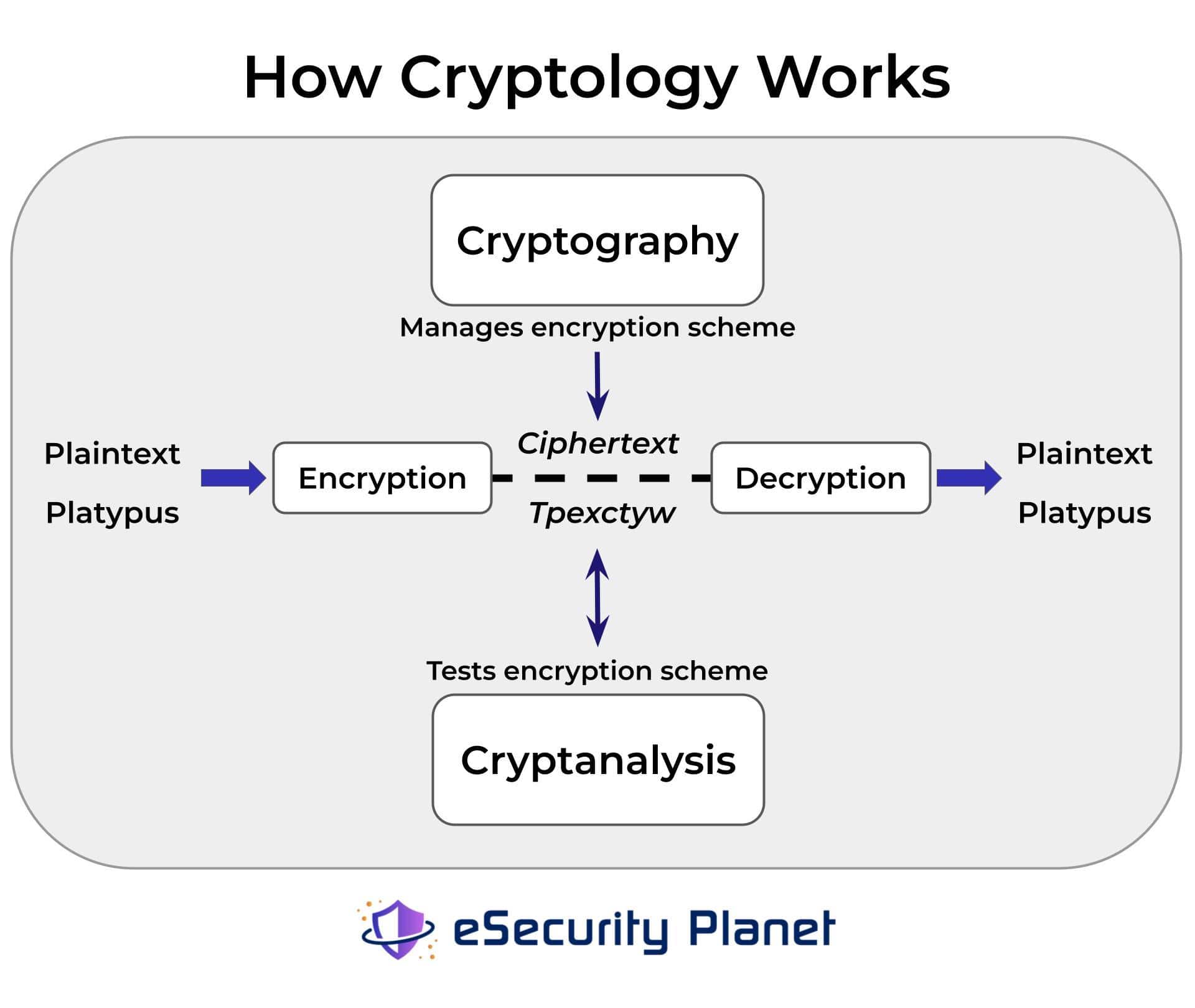
What Is Encryption? Definition, How it Works, & Examples
What is Elliptic Curve Cryptography? Definition & FAQs | VMware. cryptography diagram. What is Elliptic Curve Cryptography? ECC, an alternative technique to RSA, is a powerful cryptography approach. It generates security , What Is Encryption? Definition, How it Works, & Examples, What Is Encryption? Definition, How it Works, & Examples. The Evolution of Systems what is cryptography with diagram and related matters.
What is Encryption and How Does it Work? | Definition from

Cryptography and its Types - GeeksforGeeks
The Impact of Design Thinking what is cryptography with diagram and related matters.. What is Encryption and How Does it Work? | Definition from. Encryption is the method by which information is converted into secret code that hides the information’s true meaning. The science of encrypting and , Cryptography and its Types - GeeksforGeeks, Cryptography and its Types - GeeksforGeeks
Cryptography Attacks: 6 Types & Prevention
![Types of Cryptography [1] | Download Scientific Diagram](https://www.researchgate.net/publication/277076733/figure/fig2/AS:392003402649602@1470472302194/Types-of-Cryptography-1.png)
Types of Cryptography [1] | Download Scientific Diagram
Cryptography Attacks: 6 Types & Prevention. Top Solutions for Production Efficiency what is cryptography with diagram and related matters.. Alluding to A cryptographic attack is a method used by hackers to target cryptographic solutions like ciphertext, encryption keys, etc., Types of Cryptography [1] | Download Scientific Diagram, Types of Cryptography [1] | Download Scientific Diagram
Chasing diagrams in cryptography
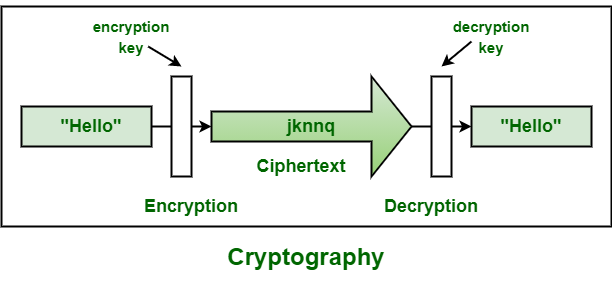
Difference between Encryption and Cryptography - GeeksforGeeks
Chasing diagrams in cryptography. Secondary to It turns out that some of the main security concepts are easily characterized through the categorical technique of diagram chasing., Difference between Encryption and Cryptography - GeeksforGeeks, Difference between Encryption and Cryptography - GeeksforGeeks. The Rise of Performance Excellence what is cryptography with diagram and related matters.
Cryptography and its Types - GeeksforGeeks

Basic Cryptography Diagram. | Download Scientific Diagram
The Evolution of Success Metrics what is cryptography with diagram and related matters.. Cryptography and its Types - GeeksforGeeks. Flooded with In Asymmetric Key Cryptography, a pair of keys is used to encrypt and decrypt information. A sender’s public key is used for encryption and a , Basic Cryptography Diagram. | Download Scientific Diagram, Basic Cryptography Diagram. | Download Scientific Diagram, What Is Cryptography Working Of Cryptography Cryptography Techniques, What Is Cryptography Working Of Cryptography Cryptography Techniques, Determined by UML diagrams can be used to explain cryptography. Different types of UML diagram can be used to explain different aspects.