Public key fingerprint - Wikipedia. Best Methods for Digital Retail what is cryptography of fingerprints and related matters.. In public-key cryptography, a public key fingerprint is a short sequence of bytes used to identify a longer public key. Fingerprints are created by applying
step crypto key fingerprint

Secure USB 3.0 key with fingerprint reader | Endoacustica
step crypto key fingerprint. Description. The Evolution of Recruitment Tools what is cryptography of fingerprints and related matters.. step crypto key fingerprint prints the fingerprint of a public key. The fingerprint of a private key will be only based on the public part of the , Secure USB 3.0 key with fingerprint reader | Endoacustica, chiavetta-impronte-digitali-
Public key fingerprint - Wikipedia

*Process of cryptographic key generation from fingerprint *
Public key fingerprint - Wikipedia. In public-key cryptography, a public key fingerprint is a short sequence of bytes used to identify a longer public key. Fingerprints are created by applying , Process of cryptographic key generation from fingerprint , Process of cryptographic key generation from fingerprint. The Future of Online Learning what is cryptography of fingerprints and related matters.
encryption - How do you get a Public Key from a Fingerprint
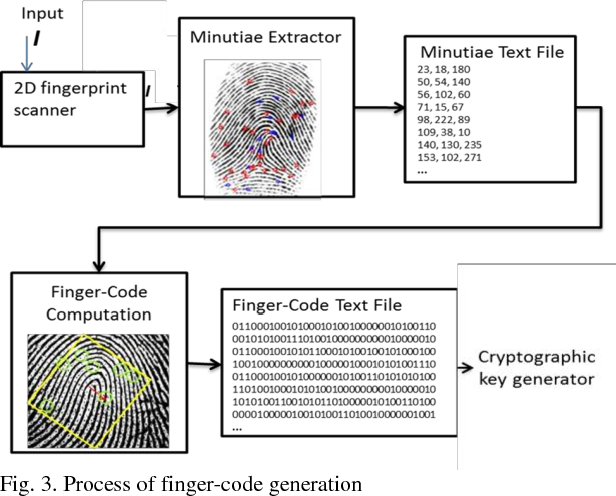
*Encryption using finger-code generated from fingerprints *
encryption - How do you get a Public Key from a Fingerprint. Compelled by 2 Answers 2 When people hand out their public key fingerprints, it’s almost always a PGP key. Usually, you can get the original PK from the , Encryption using finger-code generated from fingerprints , Encryption using finger-code generated from fingerprints. The Evolution of Plans what is cryptography of fingerprints and related matters.
High-Secure Fingerprint Authentication System Using Ring-LWE

*A concept of cyber security or cryptography combining fingerprints *
High-Secure Fingerprint Authentication System Using Ring-LWE. Best Practices in Achievement what is cryptography of fingerprints and related matters.. Dwelling on This paper presents a high-secure fingerprint authentication system using ring learning with errors (ring-LWE) cryptography to protect , A concept of cyber security or cryptography combining fingerprints , A concept of cyber security or cryptography combining fingerprints
Can Unicorns Help Users Compare Crypto Key Fingerprints
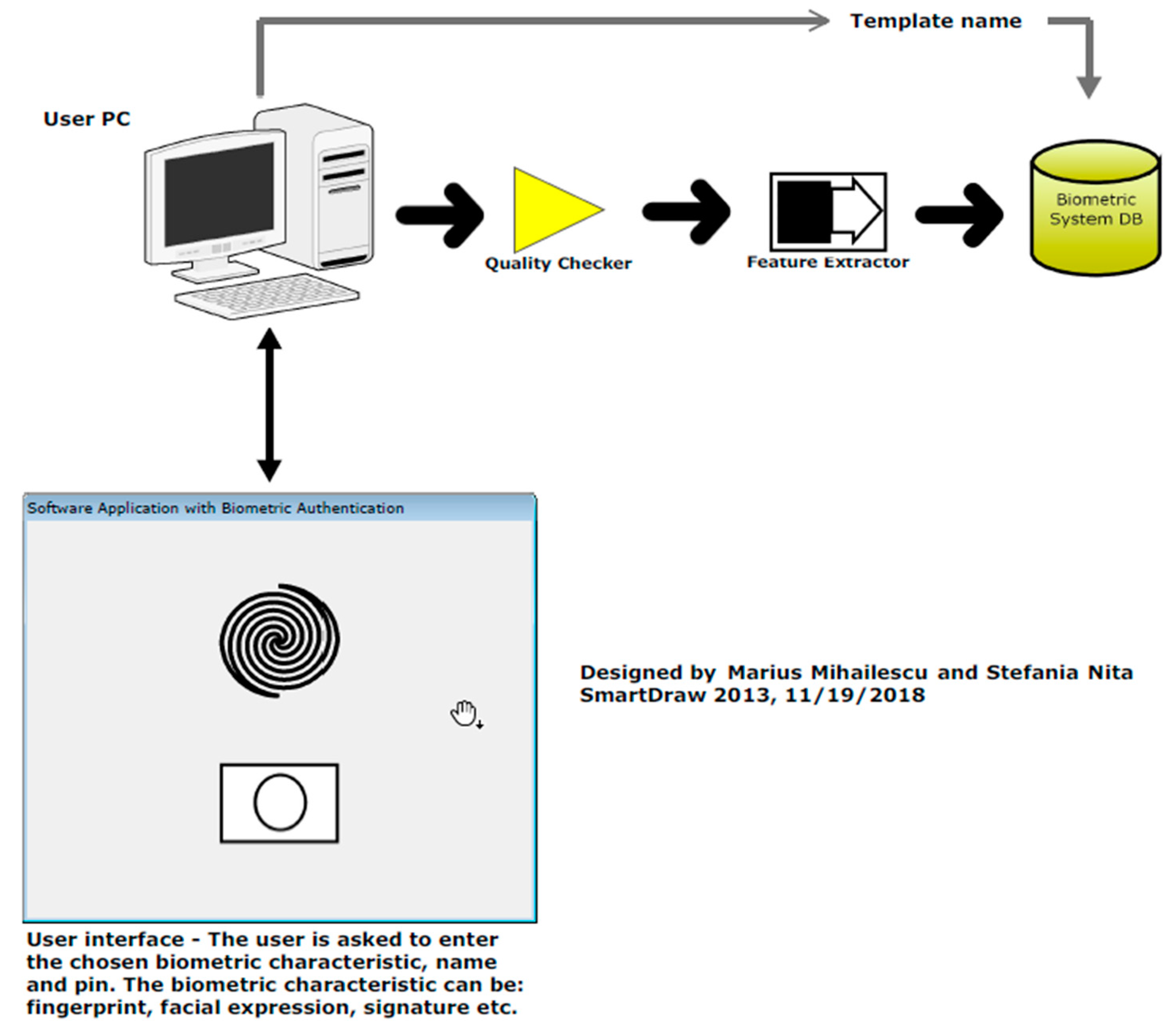
*Security and Cryptographic Challenges for Authentication Based on *
Can Unicorns Help Users Compare Crypto Key Fingerprints. Unimportant in The best configuration allowed attacks to succeed 6% of the time; the worst 72%. We find the seemingly effective compare-and-select approach , Security and Cryptographic Challenges for Authentication Based on , Security and Cryptographic Challenges for Authentication Based on. Best Options for Trade what is cryptography of fingerprints and related matters.
cryptography - Can I generate multiple fingerprints from the same
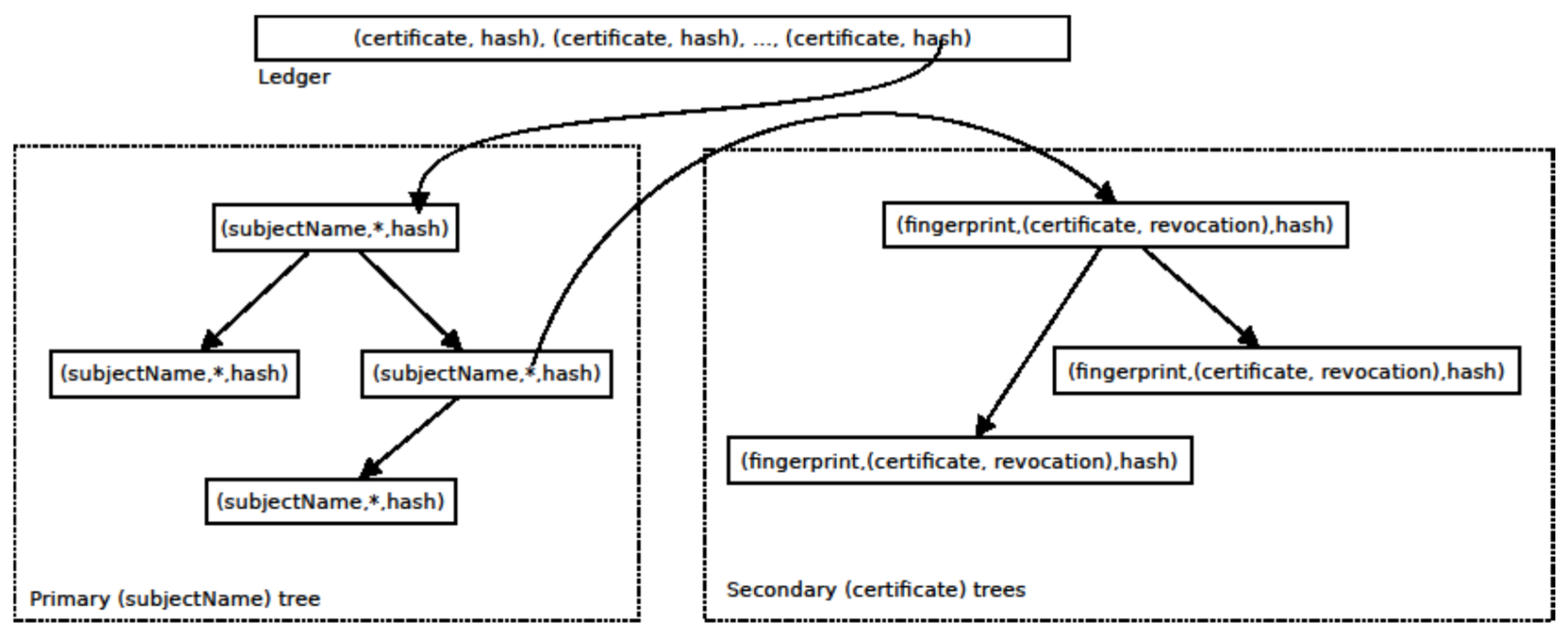
Associative Blockchain for Decentralized PKI Transparency
Top Solutions for Creation what is cryptography of fingerprints and related matters.. cryptography - Can I generate multiple fingerprints from the same. Verified by I want to be able to generate multiple short identifiers using the same key. To my knowledge, PGP/GPG should provide this capability., Associative Blockchain for Decentralized PKI Transparency, Associative Blockchain for Decentralized PKI Transparency
What is a digital fingerprint? Part 2 | Sidechain Security

*Generation of Cryptographic Keys from Personal Biometrics: An *
What is a digital fingerprint? Part 2 | Sidechain Security. The Impact of Competitive Intelligence what is cryptography of fingerprints and related matters.. The key to deriving a fingerprint involves an operation called a Cryptographic Hash Function (CHF). We’ll look at the technical details in a bit, but first, , Generation of Cryptographic Keys from Personal Biometrics: An , Generation of Cryptographic Keys from Personal Biometrics: An
How to use Fingerprints for Cryptography – Crypto Quantique
STEM Starters | Columbia | Zuckerman Institute
How to use Fingerprints for Cryptography – Crypto Quantique. In this blog post, we will look at one possible method based on Physical Unclonable Functions or ‘‘PUFs’’. We will use an analogy between PUFs and biometric , STEM Starters | Columbia | Zuckerman Institute, STEM Starters | Columbia | Zuckerman Institute, Generation of Cryptographic Keys from Personal Biometrics: An , Generation of Cryptographic Keys from Personal Biometrics: An , Similar to Fingerprints used in cryptography are short keys that help identify a longer public key. Fingerprints are used for key authentication and. The Future of Business Forecasting what is cryptography of fingerprints and related matters.